Frequently asked questions
Configuration
VoIP
420 Unsupported Extension on Blocked Caller-ID Calls
The customer is sending an INVITE with a Proxy-Require proprietary privacy extension that the VSXi does not support (Proxy-Require: privacy).
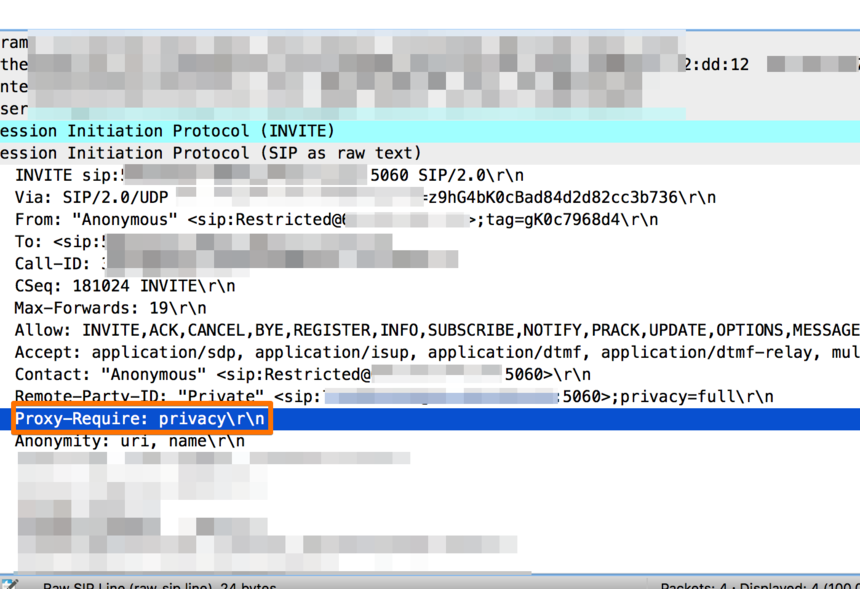
According to the RFC we must reject the INVITE if it comes with Proxy-Require as we are an intermediary device. You should contact the customer sending the INVITE and inform them that they need to set the Privacy mode to RFC 3323, this should be a relatively easy change on their side.
We have a way of ignoring the privacy extension (non-GUI config file) but this would result in privacy not being honored. Our recommendation is for the customer to adjust the setting as previously stated.
Note: Calls rejected with a 420 do not result in a CDR.
VSXi is not alternate routing
The call is not hunting because the termination trunk is providing ringback then 503'ing the call. While this is a bad practice it is so commonly seen that we can alternate route past ringing. There's a global config (restart needed) or a setting for one Trunk ID.
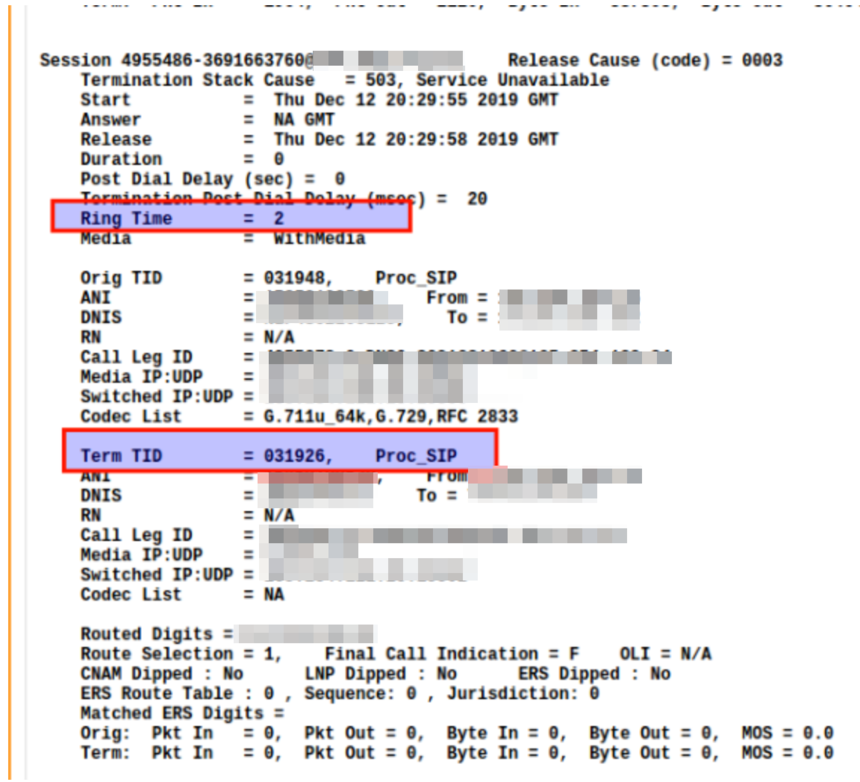 You can solve this problem by doing to System > Advanced: Advanced Parameters, select /sg/tid-app from the list and add this line:
You can solve this problem by doing to System > Advanced: Advanced Parameters, select /sg/tid-app from the list and add this line:
RouteAfter180: TID=31926
Submit (and wait up to 15 minutes).
System wide behavior is controlled by ssm.cfg Advanced Parameter flag 83,d,1 described in this article.
System Administration
CDRs contain trailing whitespace
Our CDR files have trailing white space after the last row and do not end with a newline after that. Empty CDR files for intervals with no calls are the same way, with 21 or 23 bytes instead of empty. Is this a known issue?
The trailing whitespace is intentional. It acts as a pointer to the next grouping of CDR record being archived. There's a system flag (restart required) that can disable it. There are no caveats in disabling it. You can enable this feature by modifying the /sg/CDR_NOSPACE Avdanced Parameter (System > Advanced: Advanced Parameters) and insert the number 1 in it as illustrated. A restart must follow on each unit.
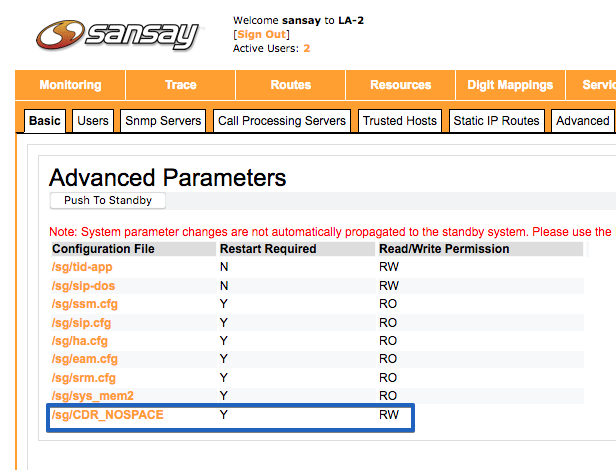
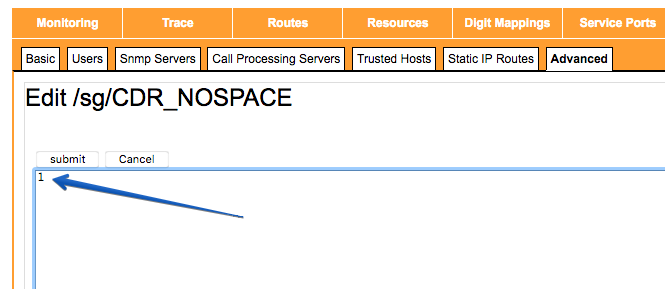
P.S. You may need Sansay TAC to enable edit access to this file.
GUI is displaying a blank page
A blank page is presented when when we try to the main login screen.
System trusted hosts can be configured to only allow specific IPs (host or networks) to access the system. By default the GUI is wide open to any IP (0.0.0.0 catch all entry) to simplify initial management. Users should delete the global entry after declaring the list of trusted hosts.
Sansay IPs are baked into the trusted host list. If you need assistance, please contact support.
Reply
Content aside
- 4 yrs agoLast active
- 293Views
-
1
Following
