How to Obtain, Renew and Manage your STIR/SHAKEN Certificate
This article illustrates the three simple steps to obtain a STIR/SHAKEN certificate using Sansay STI-CA web portal.
Pre-requisites:
- Approval from STI-PA. Related article: Working with the STI-PA https://support.sansay.com/t/p8hlsht/working-with-the-sti-pa#approval-phase
- STI-PA API User creation: https://support.sansay.com/t/y4hz3jc#sti-pa-api-user. This is used for SPC token acquisition with Sansay STI-CA.
STI-CA Web Portal
Obtaining your first certificate

After completing registration with the STI-PA and creating an API user, Sansay Support will create an STI-CA account on Sansay's web portal. Here are the three steps to obtain your certificate.
Step 1: Private Key
Create a private key.
The private key can be securely generated via the web portal or imported.

Upon generating the key you will have the option to download and delete it.
Step 2: Certificate Signature Request
The Certificate Signature Request (CSR) contains information related to your organization. This is very similar to standard TLS certificates with the difference that CSRs carry your SPC.

Step 3: Generate Certificate
A certificate is generated using a previously generated or uploaded key/CSR combination. You will need to specify an effective date, the certificate lifespan (1-365 days). Once the certificate is generated you will have the option to download it. You won't need to do anything with the downloaded cert as this certificate is hosted by Sansay's geo-redundant and highly available STI-CR (Certificate Repository) but you have the option to host it yourself if you prefer.

Re-issuing or Renewing a Certificate
Certificates can be re-issued or renewed at any time via the STI-CA web portal. Please follow these steps:
- Access the Sansay STI-CA web portal.
- Navigate to the CSR tab.
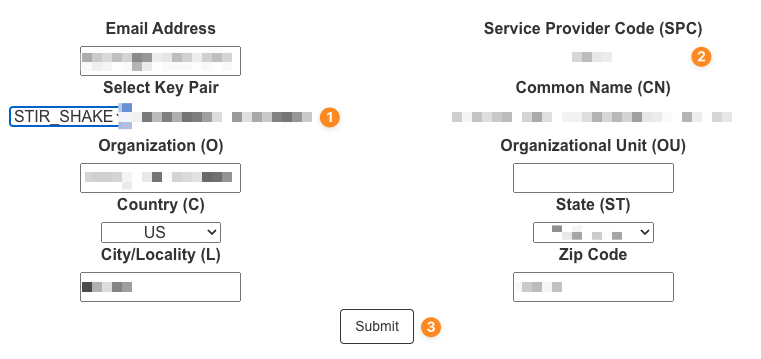
- Create a new CSR (Certificate Signature Request) by clicking on "Add"
- Specify a private key (Key Pair). Once you select a key the SPC Code will display automatically.
- Fill out the remaining fields with your organization's current details.
- Click Submit. (A CSR file will be downloaded automatically for your own records).
- Navigate to the Certificates tab.
- Create a new certificate by clicking on "Add"
- Select a CSR (when you do, the Private Key will auto-populate).
- Specify Start Time
- # of Days (Up to 365.
- Submit.
- A certificate file will be downloaded automatically for your own records. In most cases just the STI-CR URL is needed to be updated on your signing platform.

Note: To adhere with new standards please note that when a certificate is renewed it will have a new URL. The URL will need to be updated on the system responsible for call signing/STI-AS.
Automated Renewals
Automated certificate renewal is accomplished by whitelisting the Service Provider's STI-AS infrastructure that will be talking to STI-CA. This system must have been previously whitelisted by the STI-PA infrastructure. The source IP address of the system(s) renewing certificates will need to be added under "My Account".

For Service Providers with third-party STIR/SHAKEN software, ACME client integration is provided with prepaid professional services.
Re-keying Process
The process of re-keying a certificate involves creating a new private key, CSR and certificate. This is usually done for security reasons, such as if the original private key has been compromised or lost. Customers using automated certificate renewal are less likely to require a re-key as the key is regularly refreshed.
Re-keying a certificate is similar to obtaining a new certificate, but with the potential to cause service disruption. The steps to re-key a certificate are:
- Log in to the STI-CA portal.
- Generate a new private key.
- Create a CSR (Certificate Signing Request).
- Issue a new certificate using the new private key and CSR.
- Update existing STI infrastructure to use the new private key and certificate URL (if applicable).
- When re-keying a Sansay NSS system, you will first need to import the new keystore and then update the keystore to all applicable switche/SBCs. Screenshots below. This is done under STI-AS > Configuration.
- Add the new keystore.
- Under "Switches" replace the existing keystore entry with the new keystore.
- When re-keying a Sansay NSS system, you will first need to import the new keystore and then update the keystore to all applicable switche/SBCs. Screenshots below. This is done under STI-AS > Configuration.
2 replies
-
After generating the certificate in the sti-ca how do I upload that certificate to the NSS's? or does the generated key/csr/cert not need to be on anything but the STI-CA?
And then what entries go into the NSS to do a blanket signing based on SBCid?
Thanks!

